Configuring a NTP client
Create
the ntp.conf file
You can use ntp.client file as template and edit ntp.conf
#cd /etc/inet# cp ntp.client ntp.conf
# An example file that could be
copied over to /etc/inet/ntp.conf; it
# provides a configuration for a
host that passively waits for a server# to provide NTP packets on the ntp multicast net.
#
server 192.168.10.6 prefer
server 172.16.0.2
driftfile /var/ntp/ntp.drift
multicastclient 224.0.1.1
#
Save and
exit from ntp.conf
Check the NTP server reachability and response to NTP client:
# ntpdate -d 192.168.10.6
30 Jun 12:51:46 ntpdate[9927]: ntpdate
3-5.93e+sun 03/06/05 23:16:45 (1.4)transmit(192.168.10.6)
receive(192.168.10.6)
transmit(192.168.10.6)
receive(192.168.10.6)
transmit(192.168.10.6)
receive(192.168.10.6)
transmit(192.168.10.6)
receive(192.168.10.6)
transmit(192.168.10.6)
server 192.168.10.6, port 123
stratum 4, precision -18, leap 00, trust 000
refid [127.127.1.0], delay 0.02591, dispersion 0.00000
transmitted 4, in filter 4
reference time: db1f46e8.a3e1a000 Thu, Jun 30 2016 12:51:12.640
originate timestamp: db1f470a.efb60000 Thu, Jun 30 2016 12:51:46.936
transmit timestamp: db1f470a.efa4d000 Thu, Jun 30 2016 12:51:46.936
filter delay: 0.02599 0.02591 0.02591 0.02591
0.00000 0.00000 0.00000 0.00000
filter offset: 0.000024 0.000012 0.000012 0.000012
0.000000 0.000000 0.000000 0.000000
delay 0.02591, dispersion
0.00000offset 0.000012
30 Jun 12:51:46 ntpdate[9927]:
adjust time server 172.16.0.2 offset 0.000012 sec
Start the
ntpd daemon
# svcadm enable
svc:/network/ntp:default
Check the ntp service status:
#svcs ntp
STATE STIME FMRI
online 10:23:44 svc:/network/ntp:default
STATE STIME FMRI
online 10:23:44 svc:/network/ntp:default
driftfile /var/ntp/ntp.drift à
The difference between your clock and the time provided by NTP servers can be
examined by viwing the drift file:
Eg:
# cat /var/ntp/ntp.drift -40.65
Once the service is running you can check which server is
sync with the client:
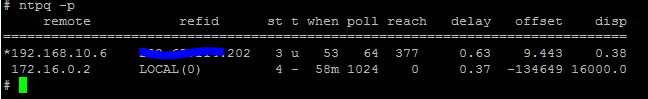
if there is * against
192.168.10.6 means NTP sync is working with particular server.
- outlyer
The peer is discarded by the clustering algorithm as an
outlyer.
+ candidat
The peer is a survivor and a candidate for the combining
algorithm.
# selected
The peer is a survivor, but not among the first six peers
sorted by synchronization distance. If the association is ephemeral, it may be
demobilized to conserve resources.
* sys.peer
The peer has been declared the system peer and lends its
variables to the system variables.
NTP default port :123 UDP










